🚀 Enterprise Azure Landing Zone – DevOps & Cloud Architecture
Microsoft Stack | Azure Landing Zone | GitOps | Kubernetes
Designed & Implemented by Mohamed Amine Hlali
Senior DevOps Engineer | Azure Cloud Architect | Microsoft Certified Trainer (MCT)
📌 Project Purpose
This project is a real, enterprise-grade Azure Landing Zone implementation, designed and built from scratch using Microsoft cloud-native services only.
The objective is to demonstrate hands-on expertise in:
- Azure Landing Zones (real implementation, not theory)
- Secure enterprise networking (Hub & Spoke)
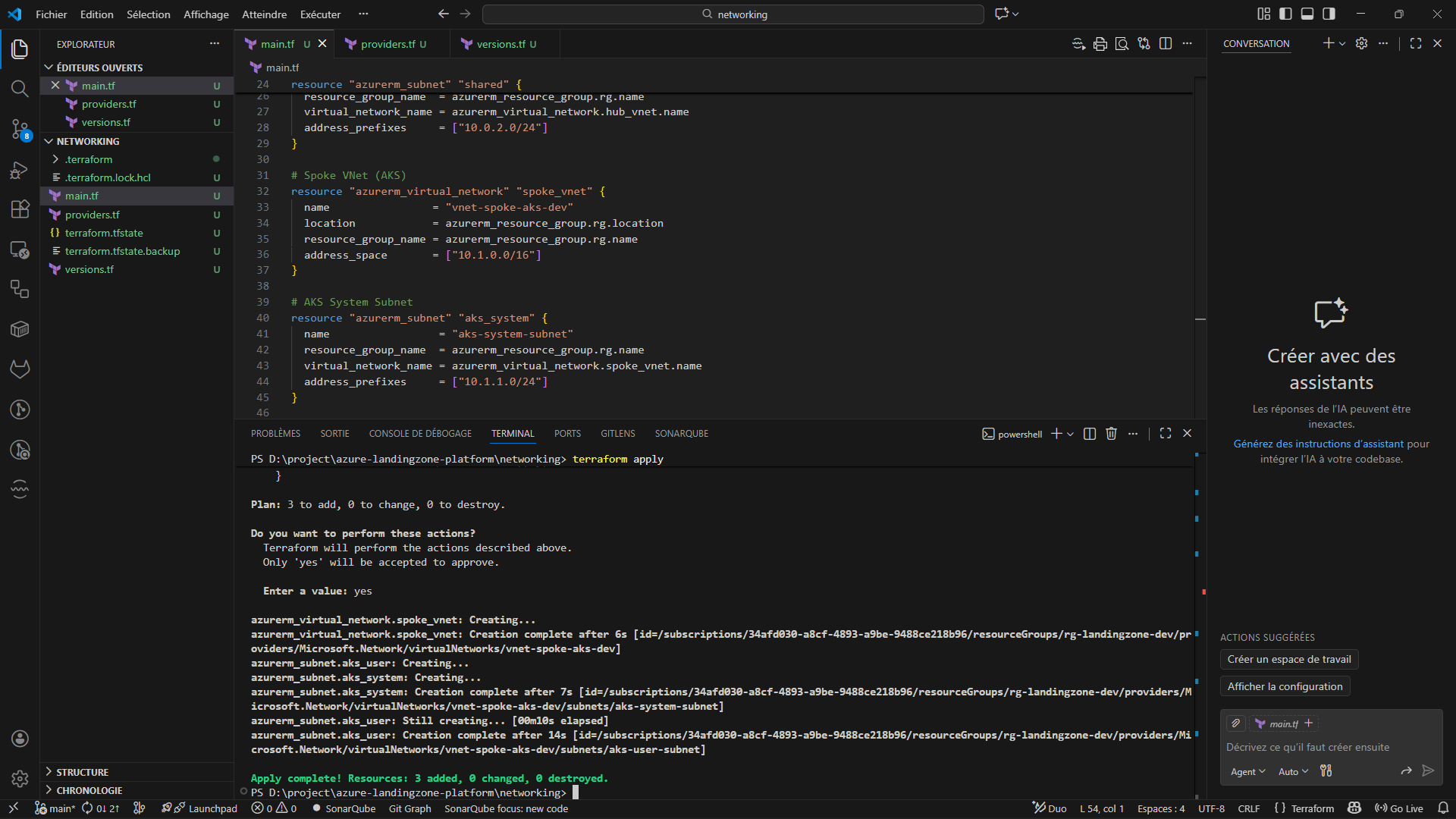
- Infrastructure as Code (Terraform)
- AKS (Private Cluster)
- CI/CD & GitOps (Azure DevOps + Argo CD)
- Observability & Monitoring (Azure Monitor, Application Insights, Grafana)
- Container security & governance
⚠️ This is not a demo or tutorial project.
It reflects production-grade architecture and decisions.
🧱 Enterprise Architecture Overview
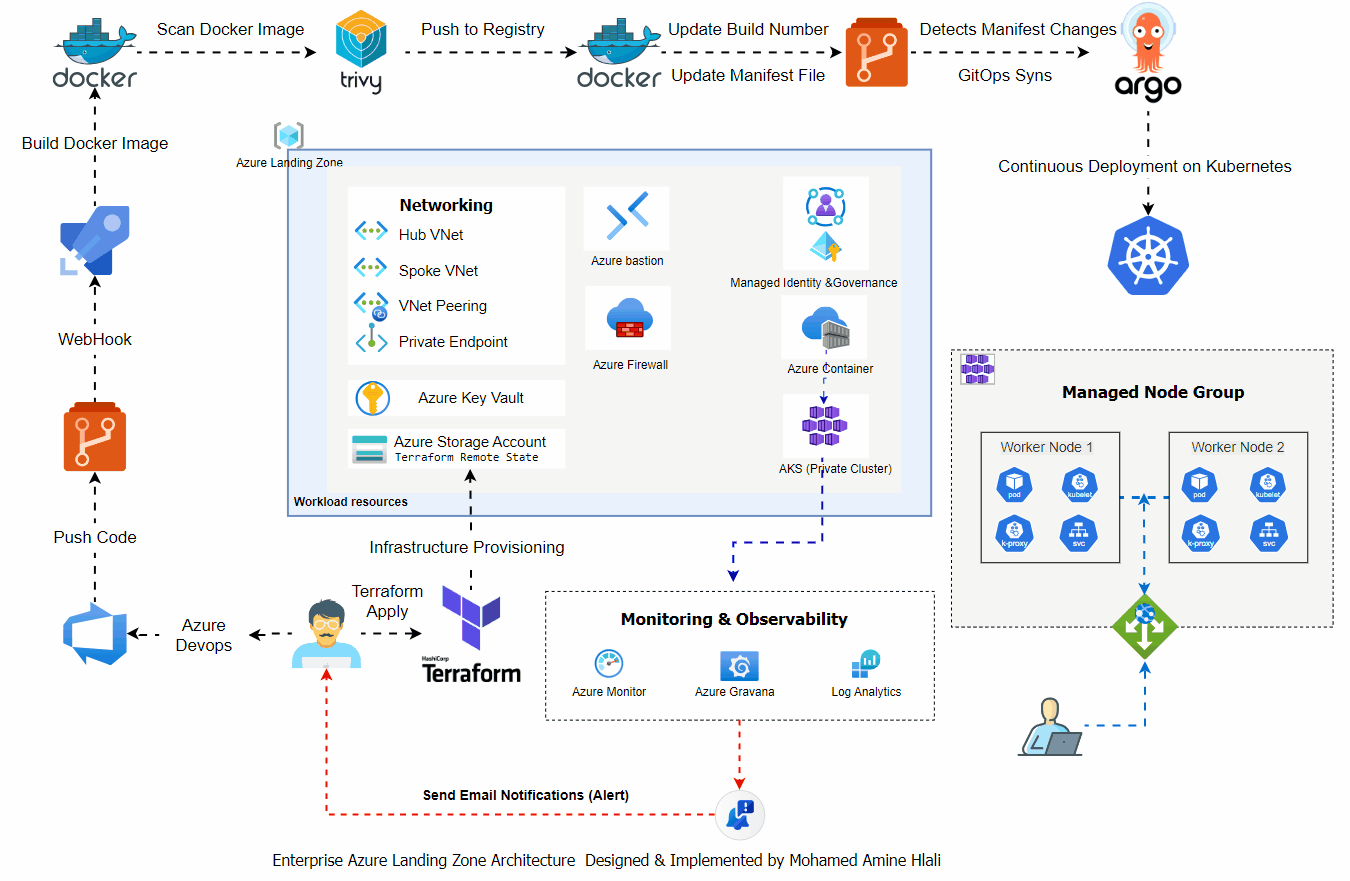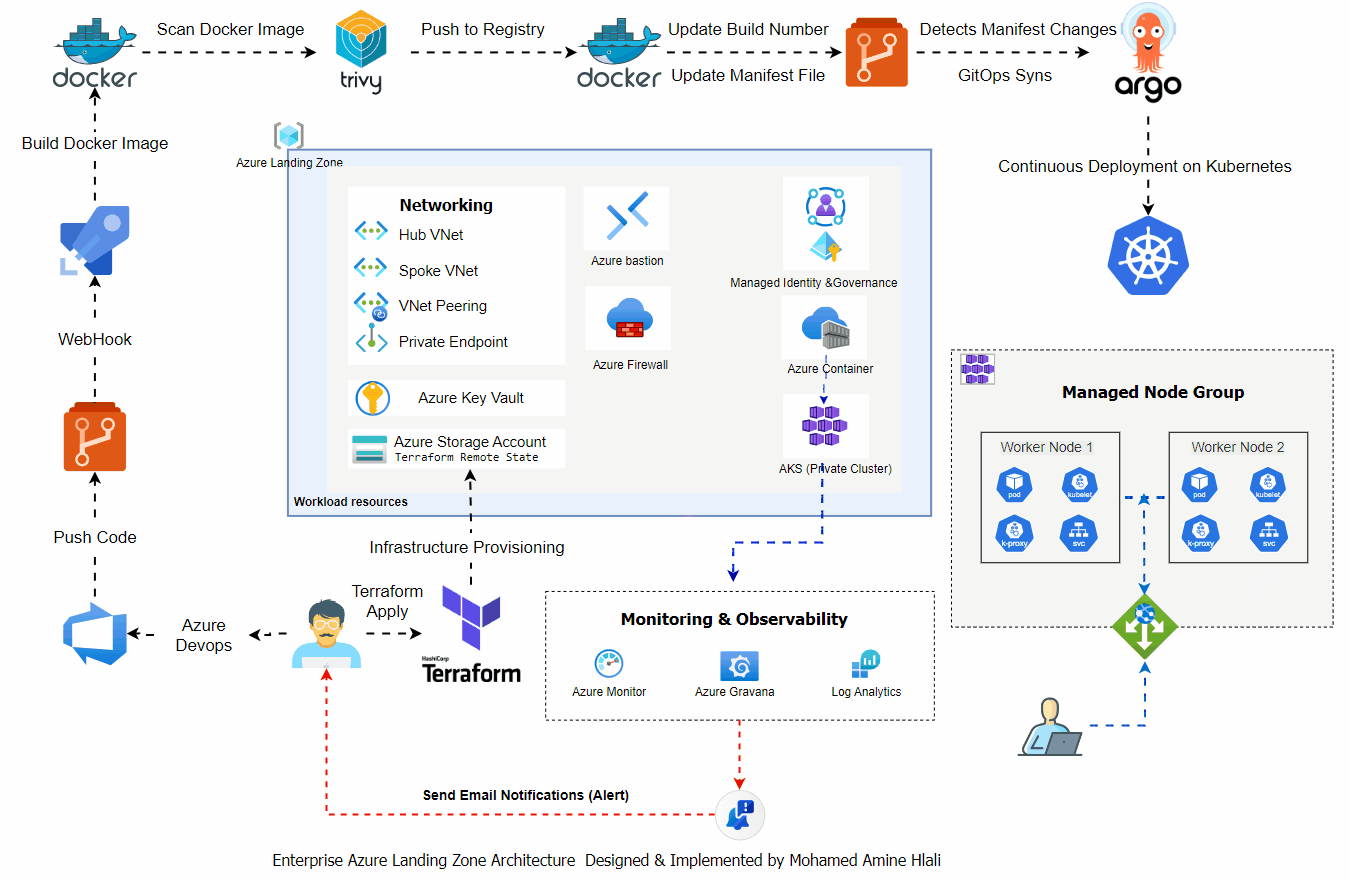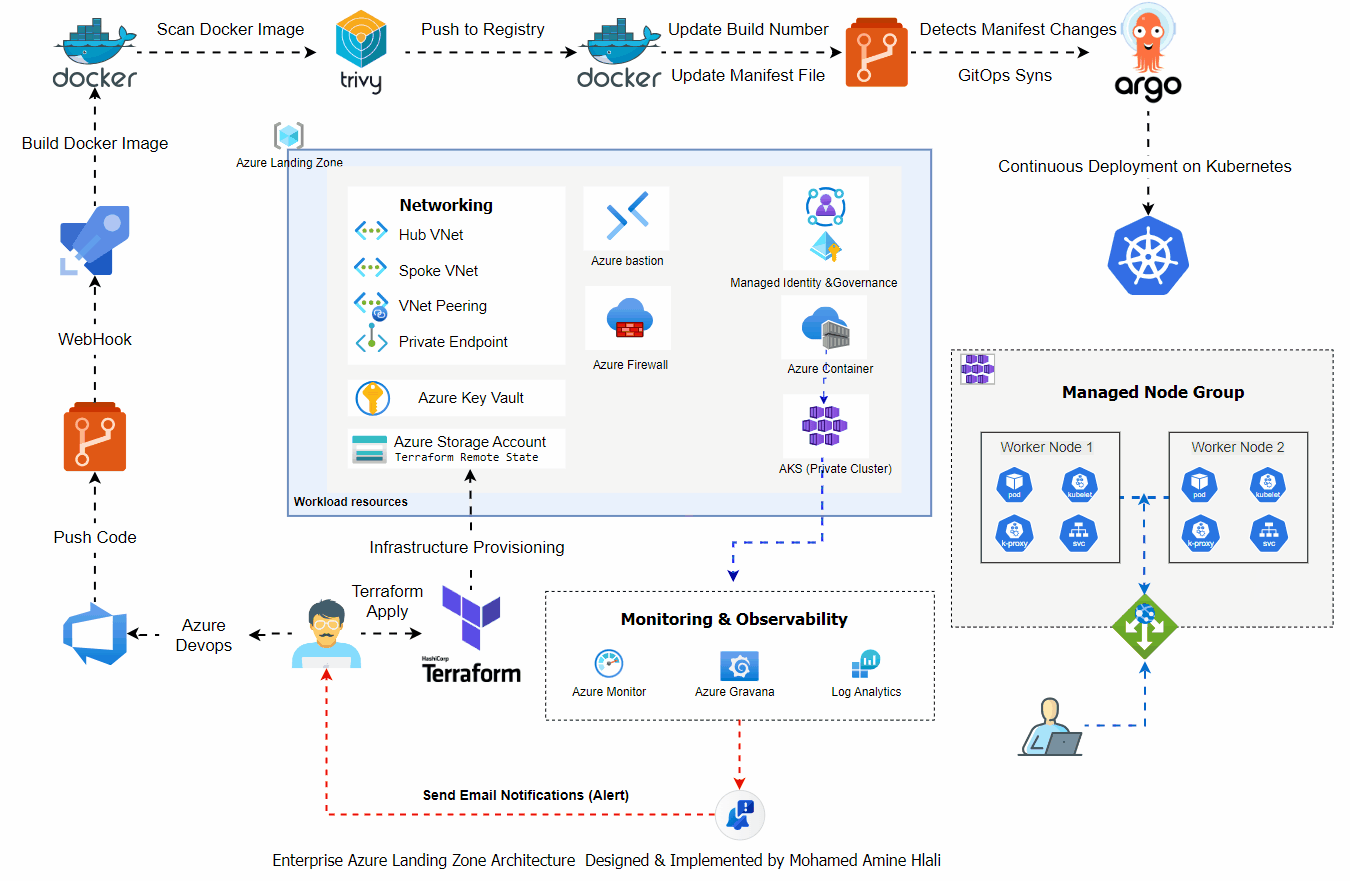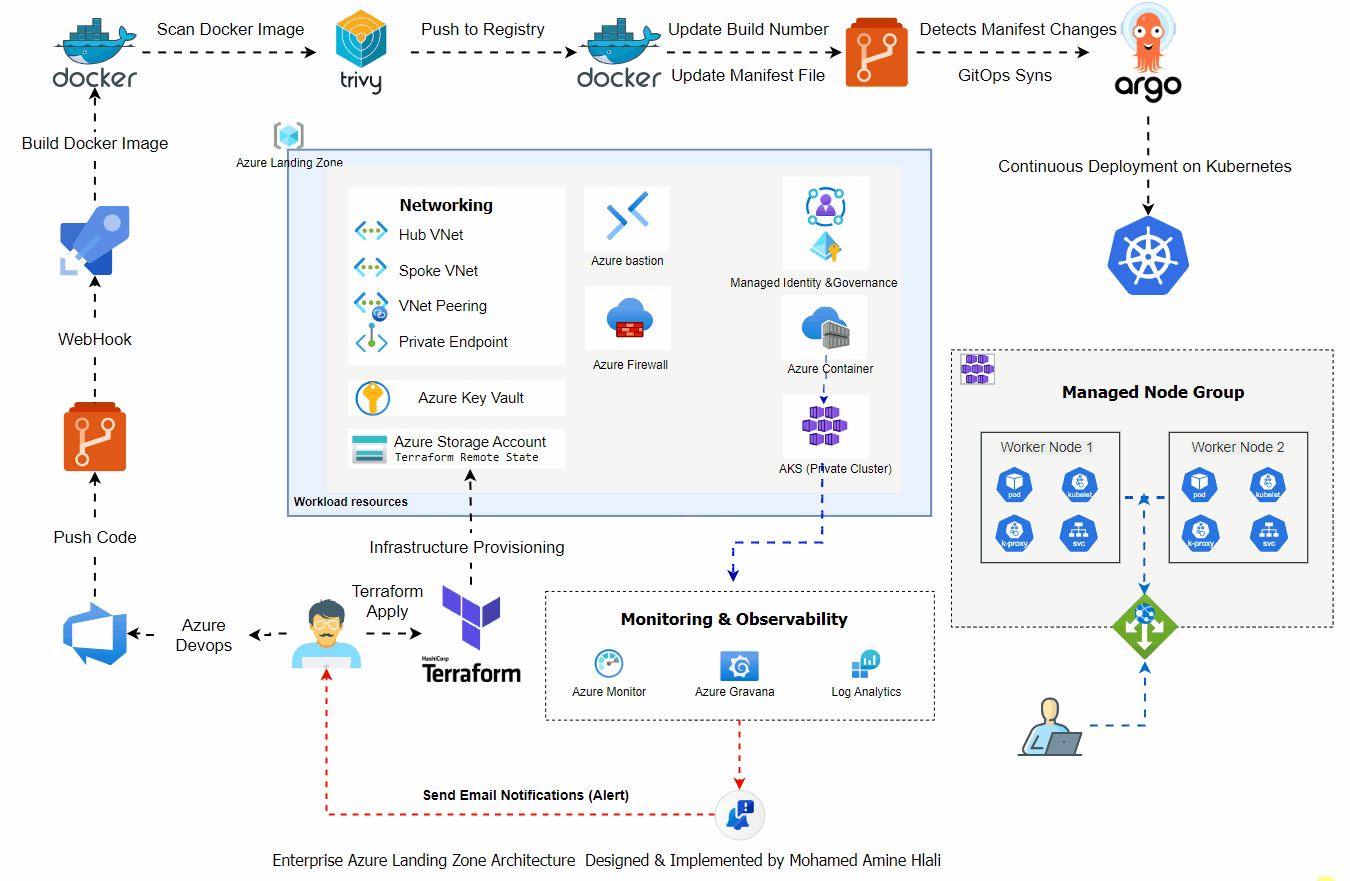
Key architectural principles:
- Fully private Kubernetes cluster
- Centralized networking & security
- GitOps-driven deployments
- Observability-first design
- Microsoft Stack only
🏗️ Azure Landing Zone – Design Areas
This Landing Zone follows Microsoft best practices across the core design areas.
🌐 Networking (Hub & Spoke)
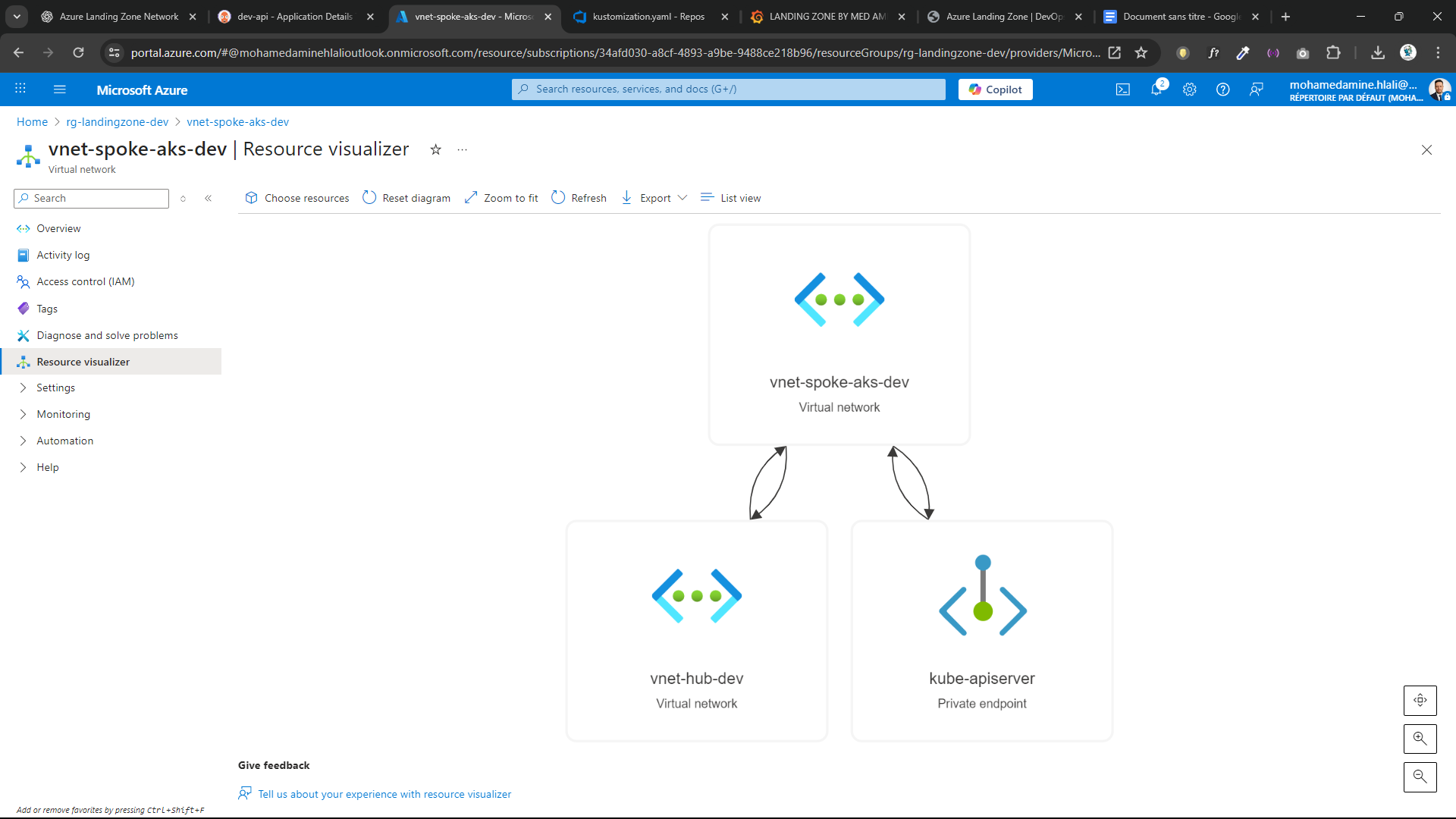
- Hub VNet for shared services
- Spoke VNet dedicated to AKS
- VNet Peering (Hub ↔ Spoke)
- Private Endpoint for AKS API Server
- Azure Firewall for traffic control
- Azure Bastion for secure administration
➡️ All networking components are provisioned using Terraform.
🔐 Security & Governance
- Private AKS cluster (no public API exposure)
- Azure Key Vault for secrets
- Managed Identity (System Assigned)
- RBAC between AKS and ACR
- Least-privilege access model
☸️ Azure Kubernetes Service (AKS)
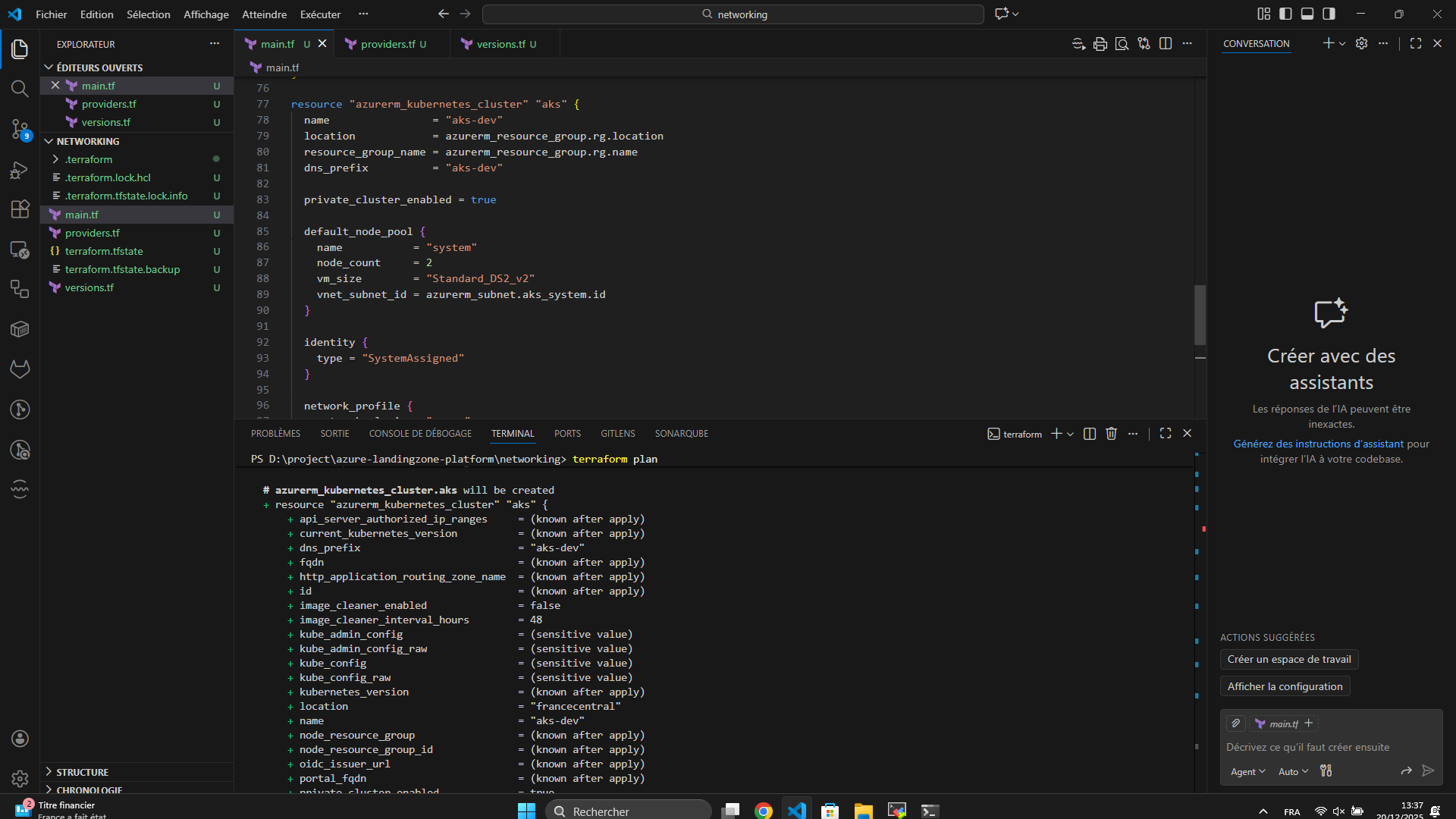
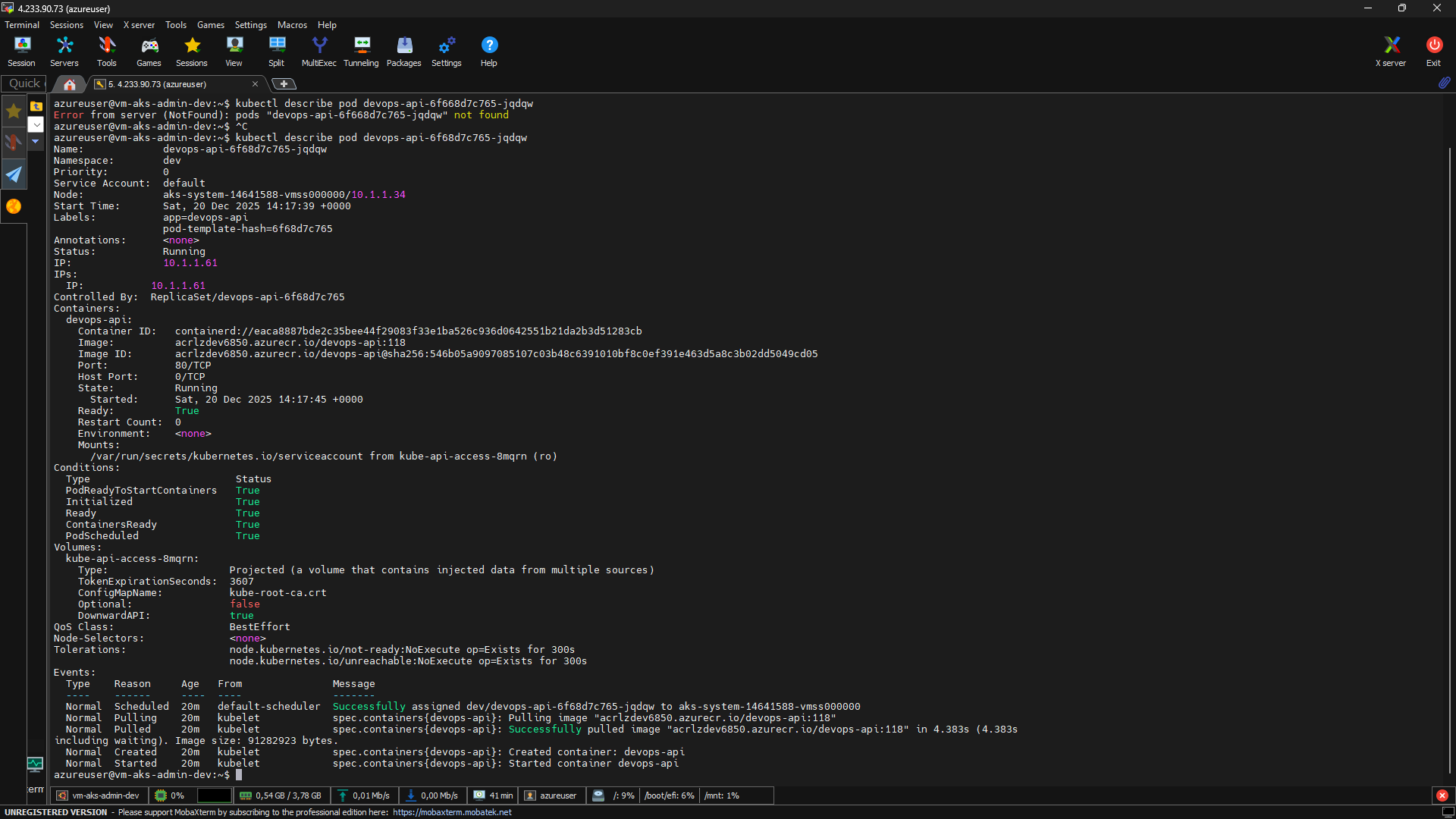
- Azure Kubernetes Service (AKS)
- Private Cluster enabled
- Managed Node Groups
- Internal Load Balancer
- Azure CNI networking
- Separation between system and workload nodes
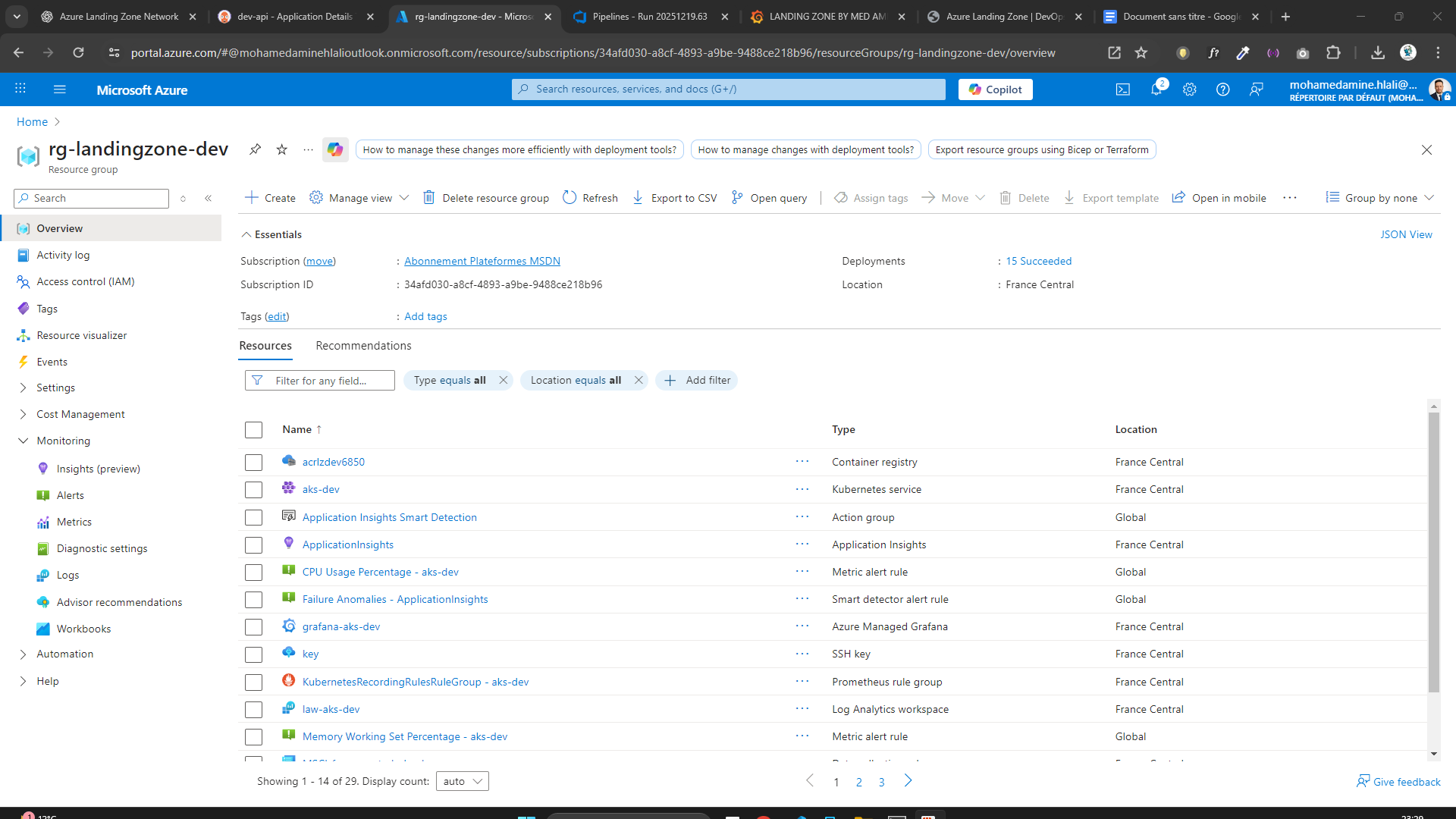
📦 Container Platform (ACR)
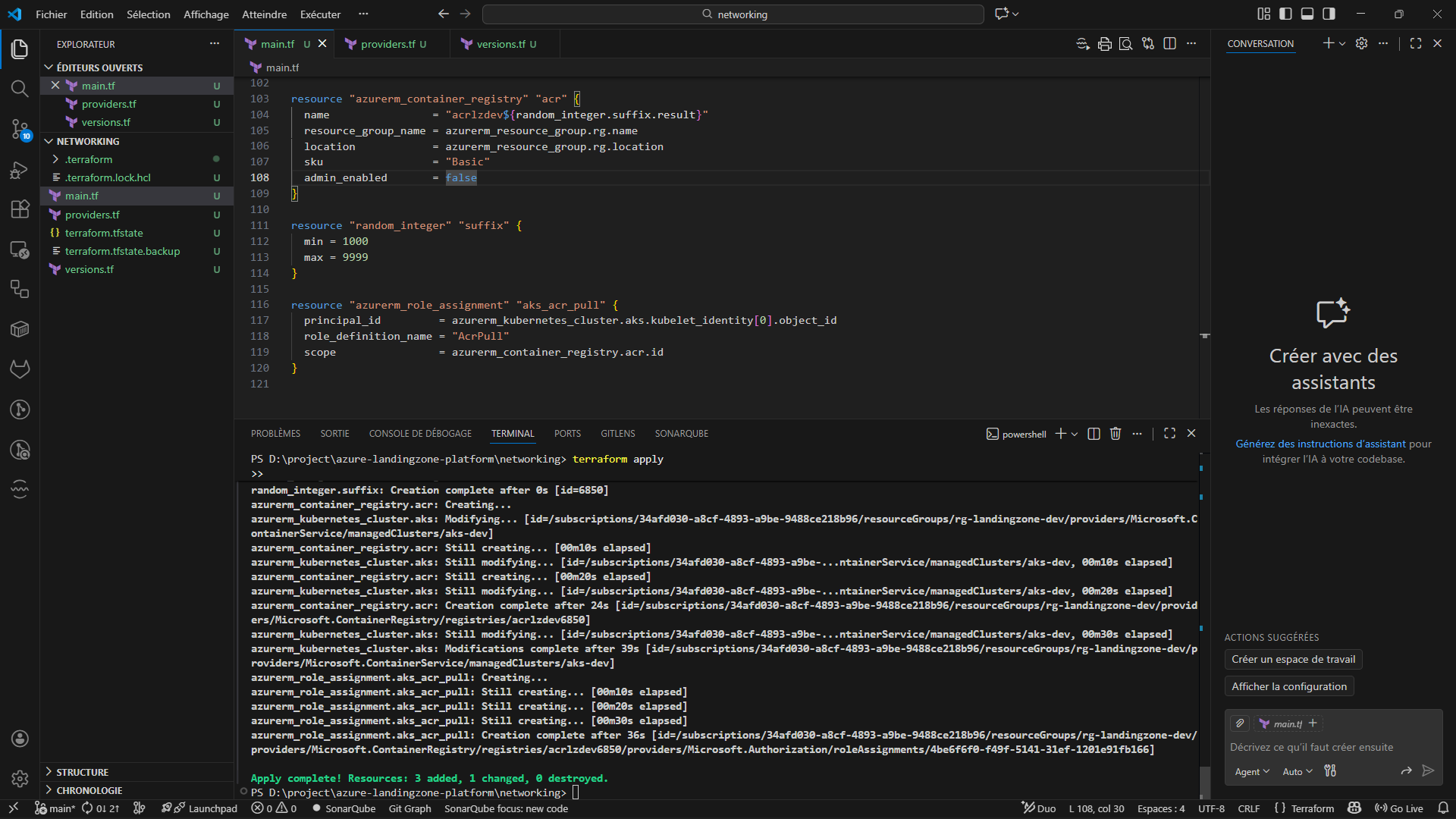
- Azure Container Registry (ACR)
- Secure image storage
- Integrated with AKS via Managed Identity
- Image pull permissions via RBAC
⚙️ Infrastructure as Code (Terraform)

- All infrastructure provisioned using Terraform
- Remote state stored in Azure Storage Account
- Idempotent and reproducible deployments
- Clear separation of concerns (networking, AKS, registry, monitoring)
🔄 CI/CD – Azure DevOps Pipeline
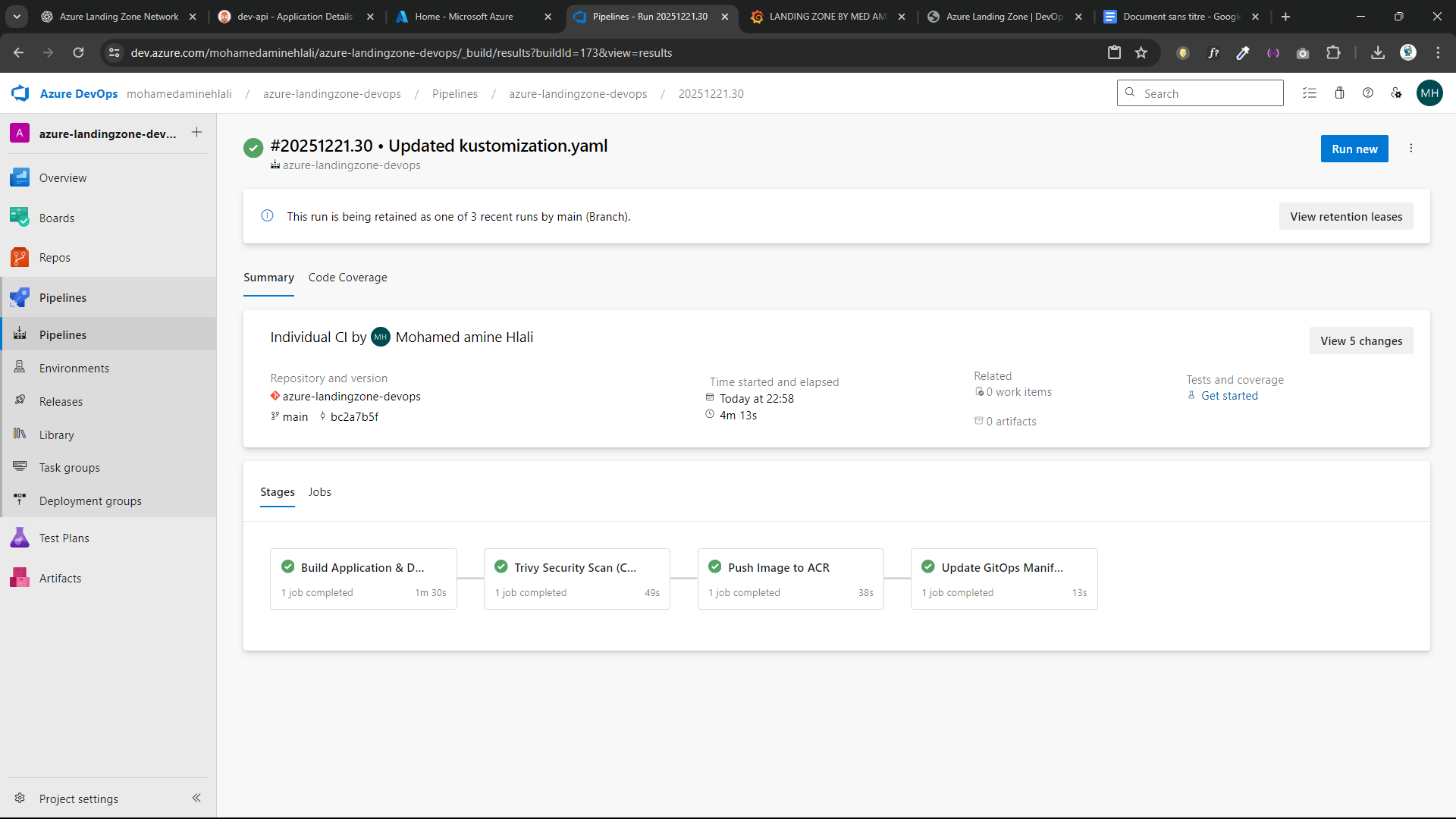
Pipeline stages:
- Build .NET Application
- Build Docker Image
- Trivy Security Scan (CRITICAL – fixable only)
- Push image to Azure Container Registry
- Update GitOps manifests (Kustomize)
- Trigger Argo CD sync
🔐 Container Security – Trivy
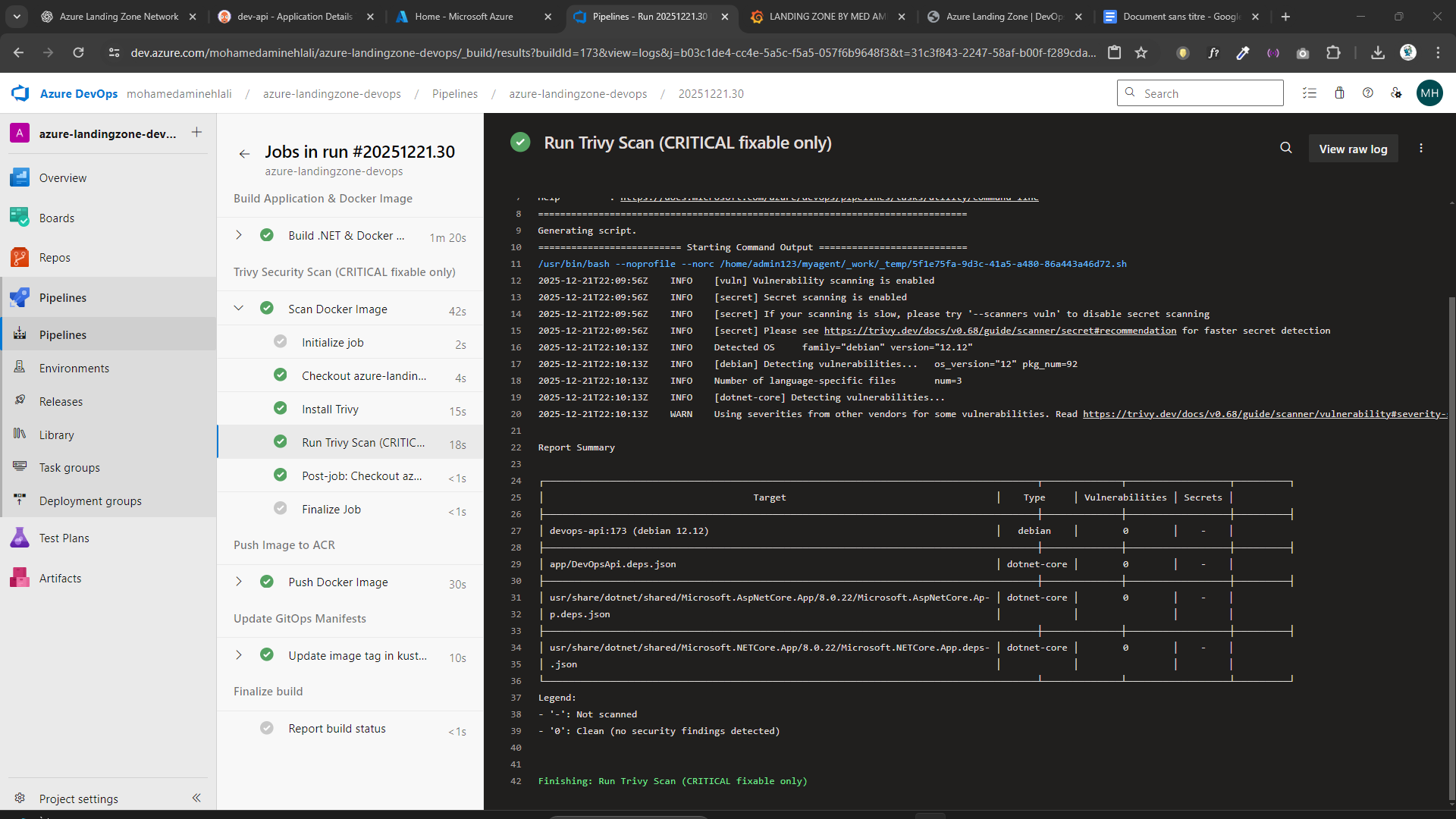
- Vulnerability scanning integrated in CI
- Only CRITICAL fixable vulnerabilities allowed
- Pipeline fails if security baseline is not met
🔁 GitOps – Argo CD
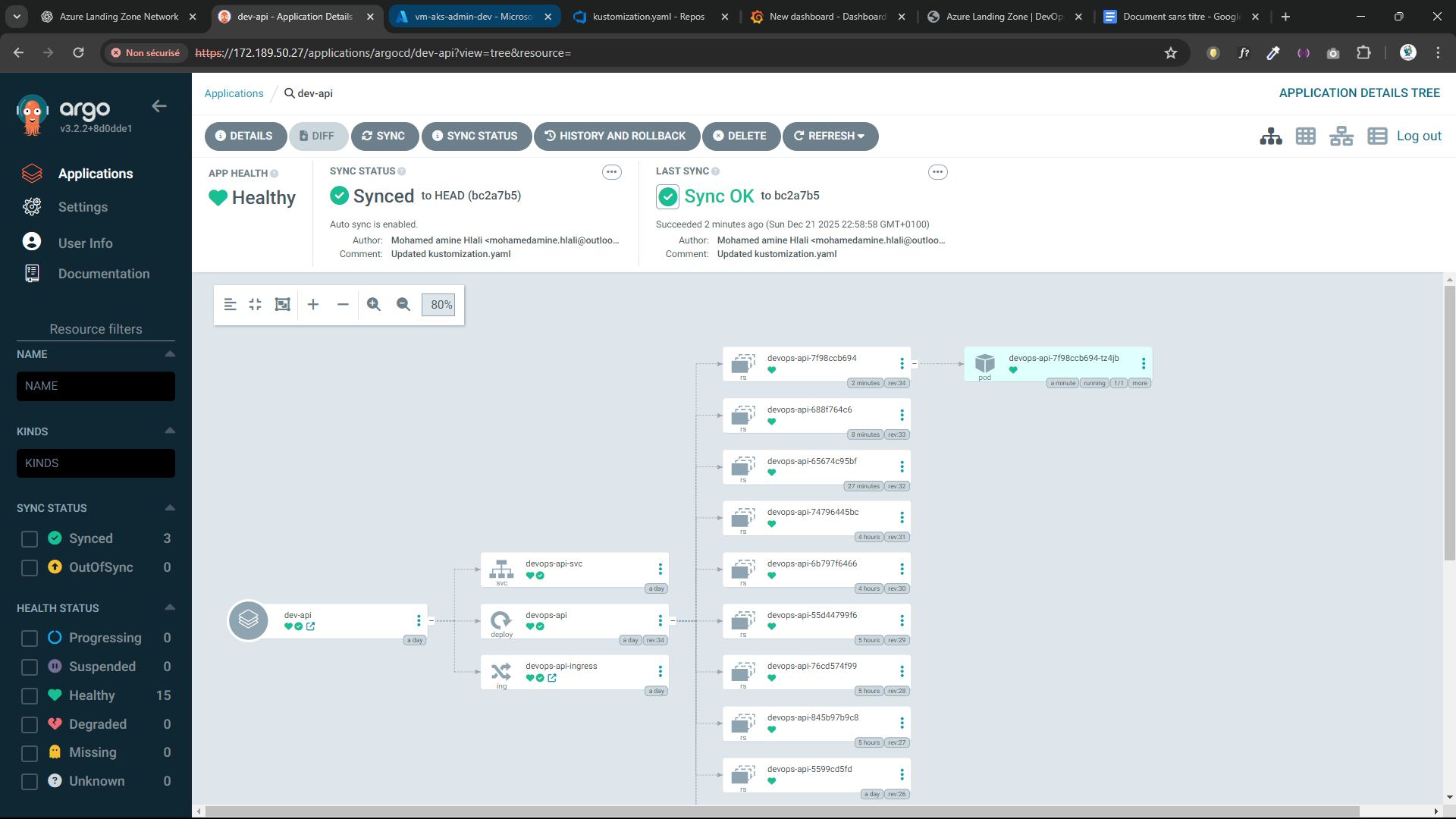
- Git is the single source of truth
- Argo CD continuously monitors manifests
- Automatic synchronization with AKS
- Visual resource tree & health status
- Easy rollback and history tracking
🧠 Application (.NET)
- .NET API containerized
- Deployed on AKS
- Exposed via Kubernetes Service & Ingress
- Real traffic handled by the cluster
📊 Observability & Monitoring
Azure Native Monitoring
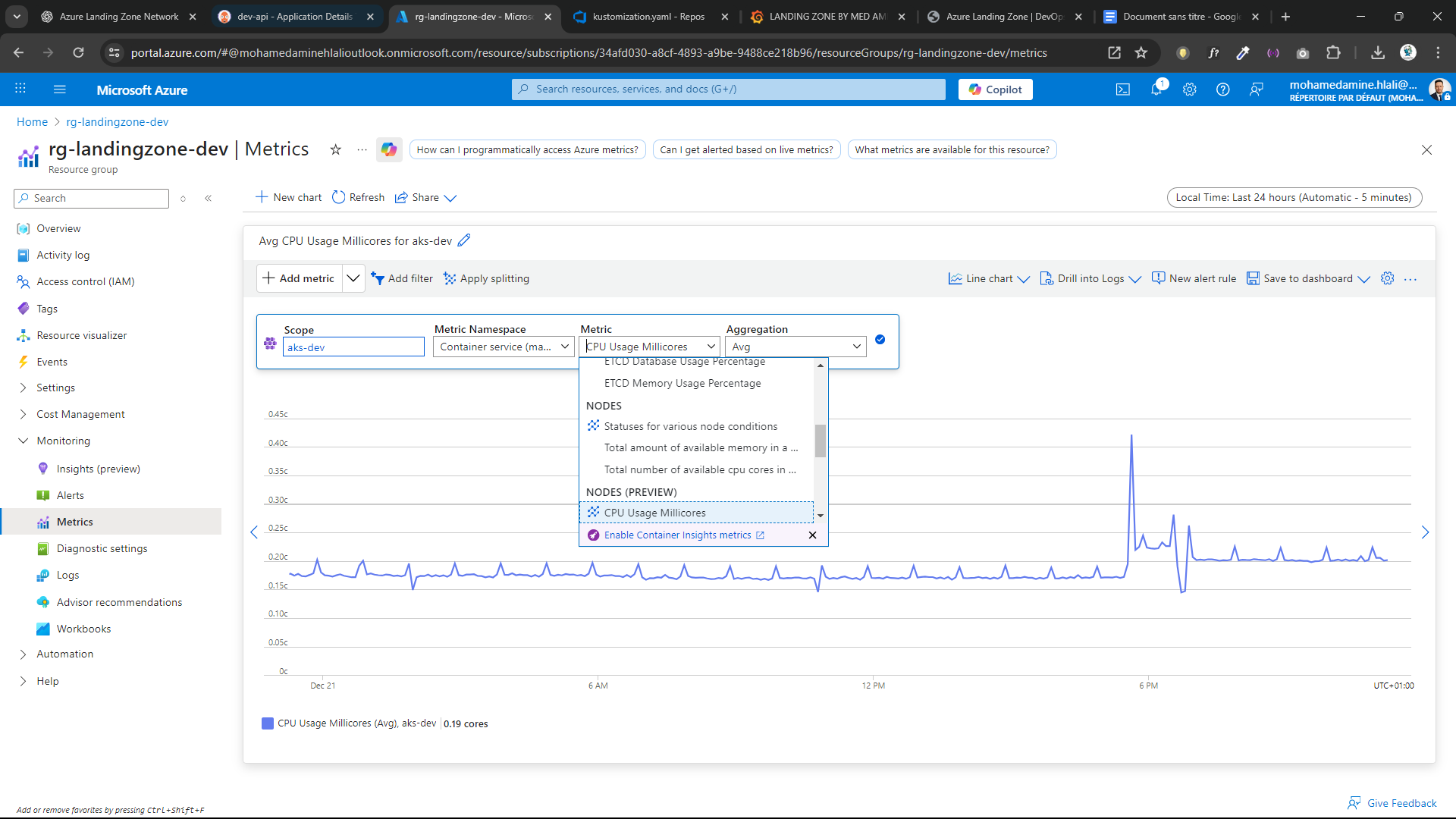
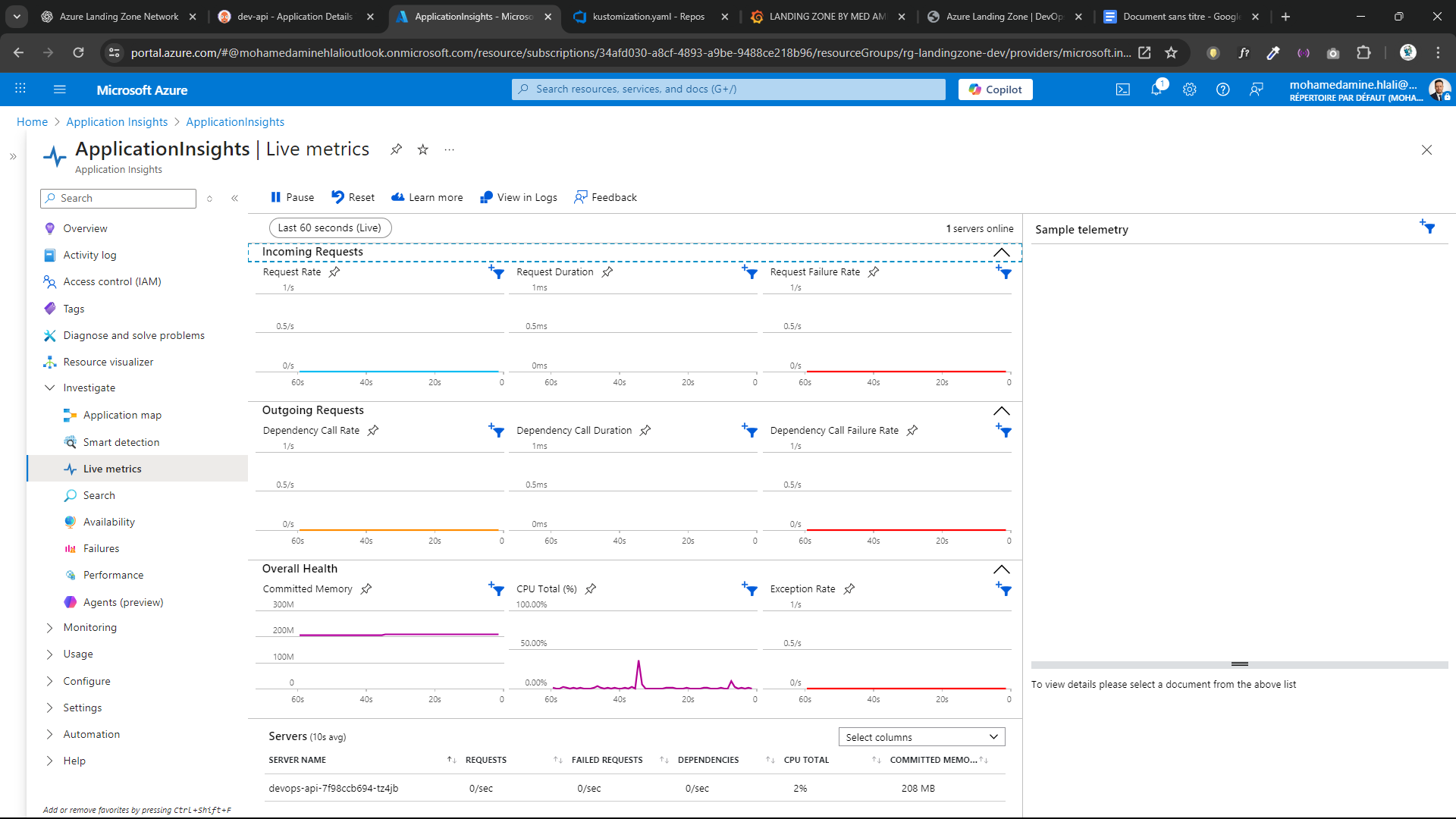
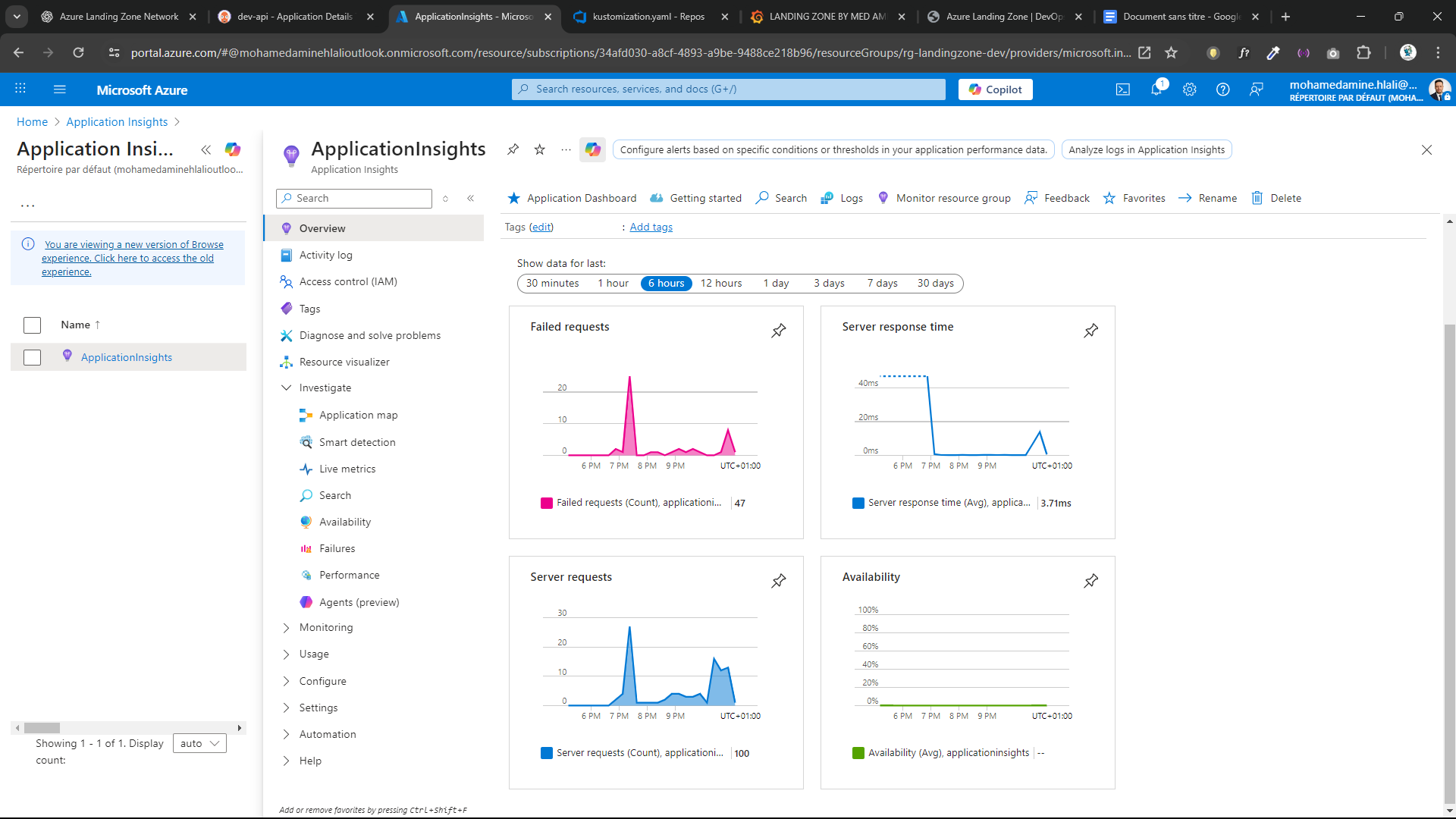
- Azure Monitor
- Log Analytics Workspace
- Application Insights
- Live metrics & smart detection
Grafana Dashboards
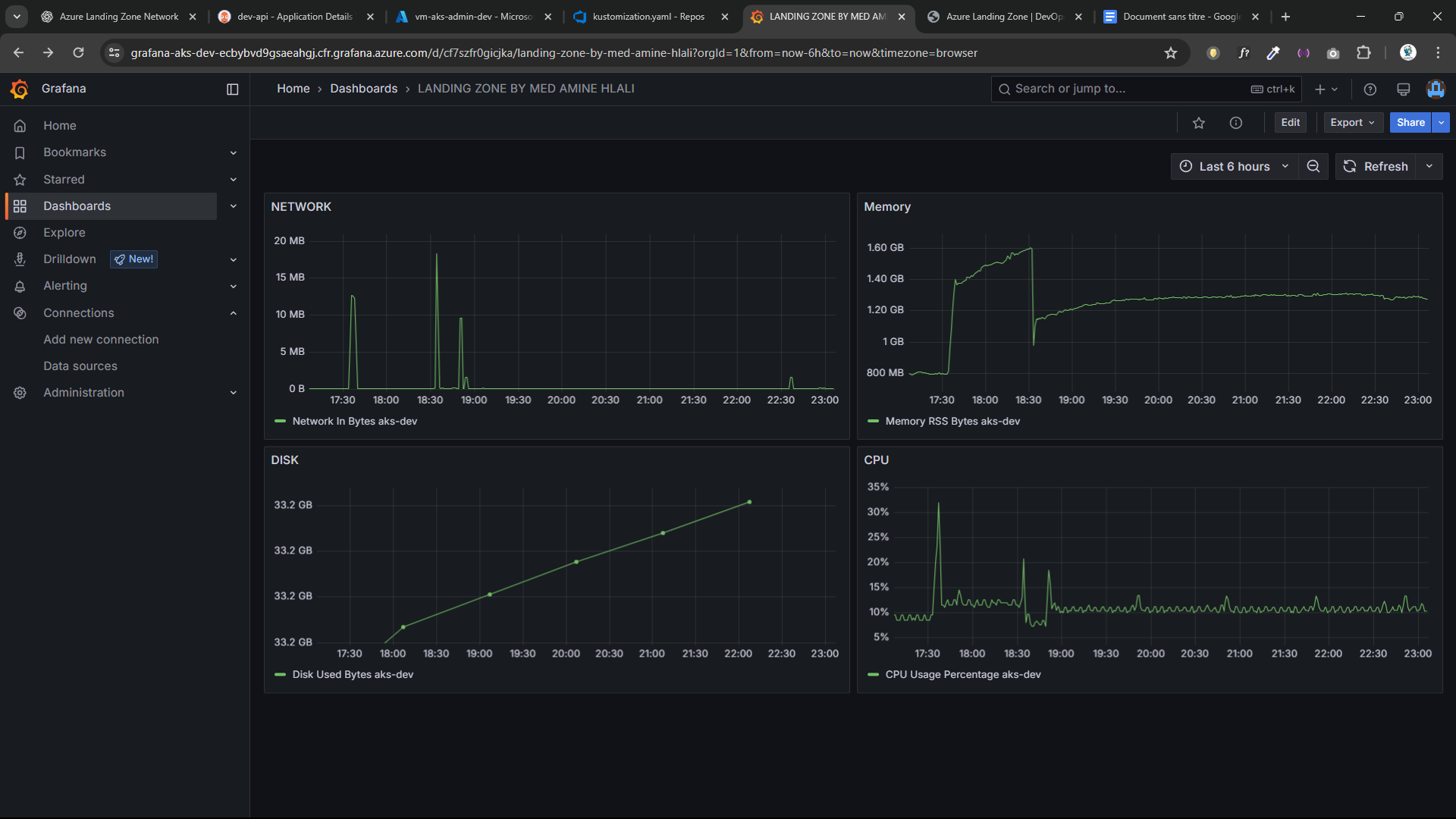
- Azure Managed Grafana
- CPU, Memory, Disk, Network
- AKS node & workload visibility
- Real-time dashboards
🚨 Alerting & Notifications
- Metric-based alerts (CPU, Memory, Failures)
- Application Insights smart detection
- Email notifications via Action Groups
➡️ Enables proactive incident detection.
🧩 Microsoft Stack Summary
✔ Azure
✔ AKS
✔ Azure DevOps
✔ Terraform
✔ Azure Container Registry
✔ Azure Monitor
✔ Application Insights
✔ Azure Managed Grafana
✔ Azure Key Vault
✔ Argo CD
✔ Docker
No third-party cloud providers. Microsoft Stack only.
🎯 Why This Project Matters
- Real Azure Landing Zone implementation
- Enterprise networking & security
- GitOps-first Kubernetes deployment
- Production-grade CI/CD
- Deep observability & monitoring
- Designed with senior-level architecture mindset
✅ Conclusion
This project demonstrates how enterprise Azure environments should be designed, focusing on:
- Security-first networking
- Infrastructure as Code
- GitOps-driven operations
- Observability & governance
🚀 More deep-dive articles coming soon.
👤 Author
Mohamed Amine Hlali
Senior DevOps Engineer | Azure Cloud Architect
Microsoft Certified Trainer (MCT)
Focused on designing secure, scalable, and observable Azure platforms using Microsoft technologies.